Safe Harbor
The following is intended to outline our general product direction. It is intended for information purposes only, and may not be incorporated into any contract. It is not a commitment to deliver any material, coe, or functionality, and should not be relied upon in making purchasing decisions. The development, release, timing, and princing of any features or functionality described for Oracle's products may change and remains at the sole discretion of Oracle Corporation.
Statements in this presentation relating to Oracle's future plans, expectations, beliefts, intentions and prospects are "forward-looking statements" and are subject to material risks and uncertainties. A detailed discussion of these factors and other risks that affect our business is contained in Oracle's Securities and Exchange Commission (SEC) filings, including our most recent reports on Form 10-K and Form 10-Q under the heading "Risk Factors." These filings are available on the SEC's website or on Oracle's website at http://www.oracle.com/investor. All information in this presentation is current as of September 2019 and Oracle undertakes no duty to update any statement in light of new information or future events.
Introduction
- I am Peter (@pjausovec)
- Software Engineer at Oracle
- Working on "cloud-native" stuff
- Books:
- Cloud Native: Using Containers, Functions, and Data to Build Next-Gen Apps
- SharePoint Development
- VSTO For Dummies
- Courses:
- Kubernetes Course (https://startkubernetes.com)
- Istio Service Mesh Course (https://learnistio.com)
Dedicated infrastructure layer to connect, manage, and secure workloads by managing the communication between them
Istio service mesh
- Open source service mesh
- Google, IBM, Lyft
- Well-defined API
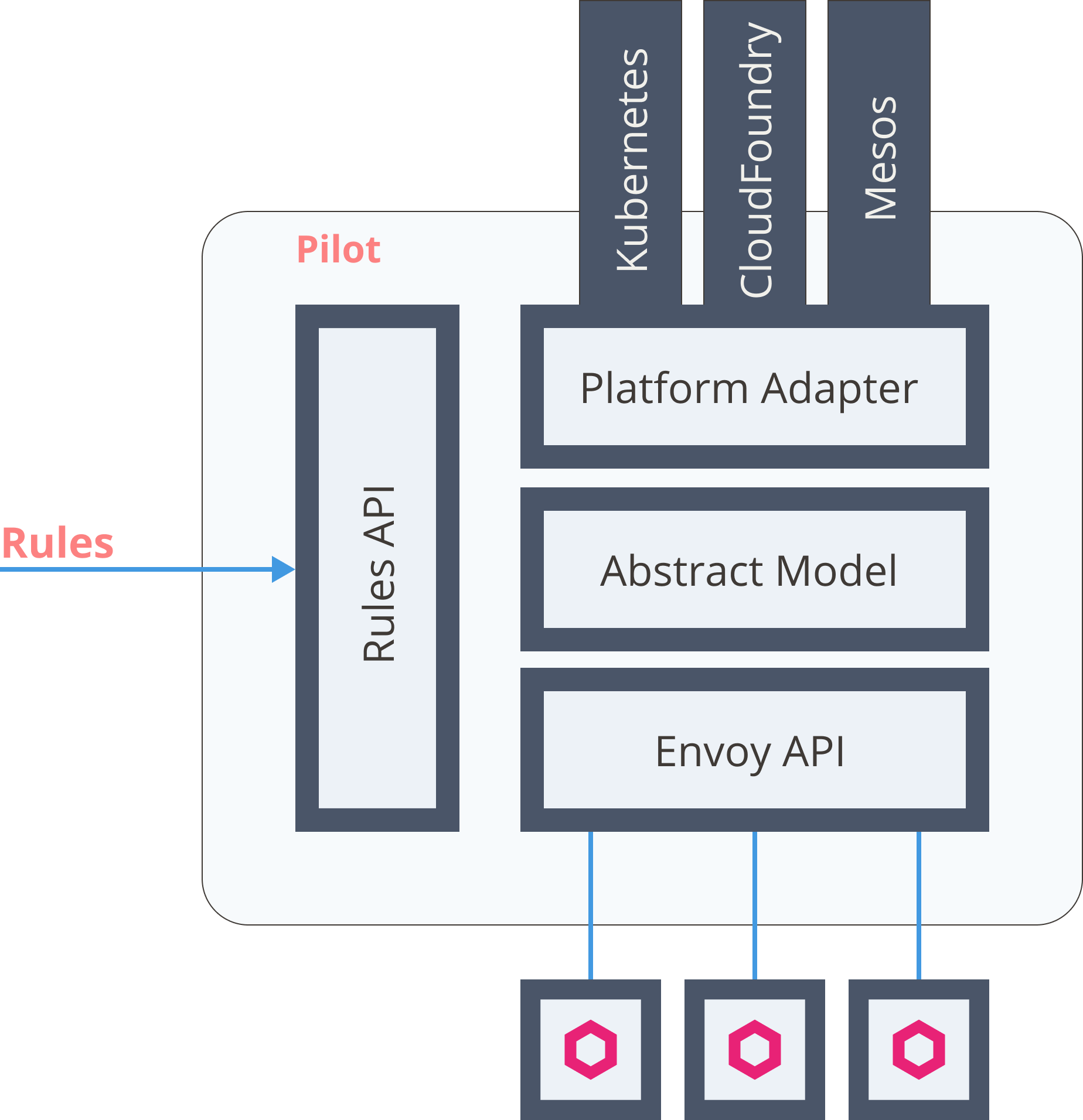
- Can be deployed on-premise, in the cloud
- Kubernetes
- Mesos
Source: https://barkpost.com/cute/sidecar-dogs/
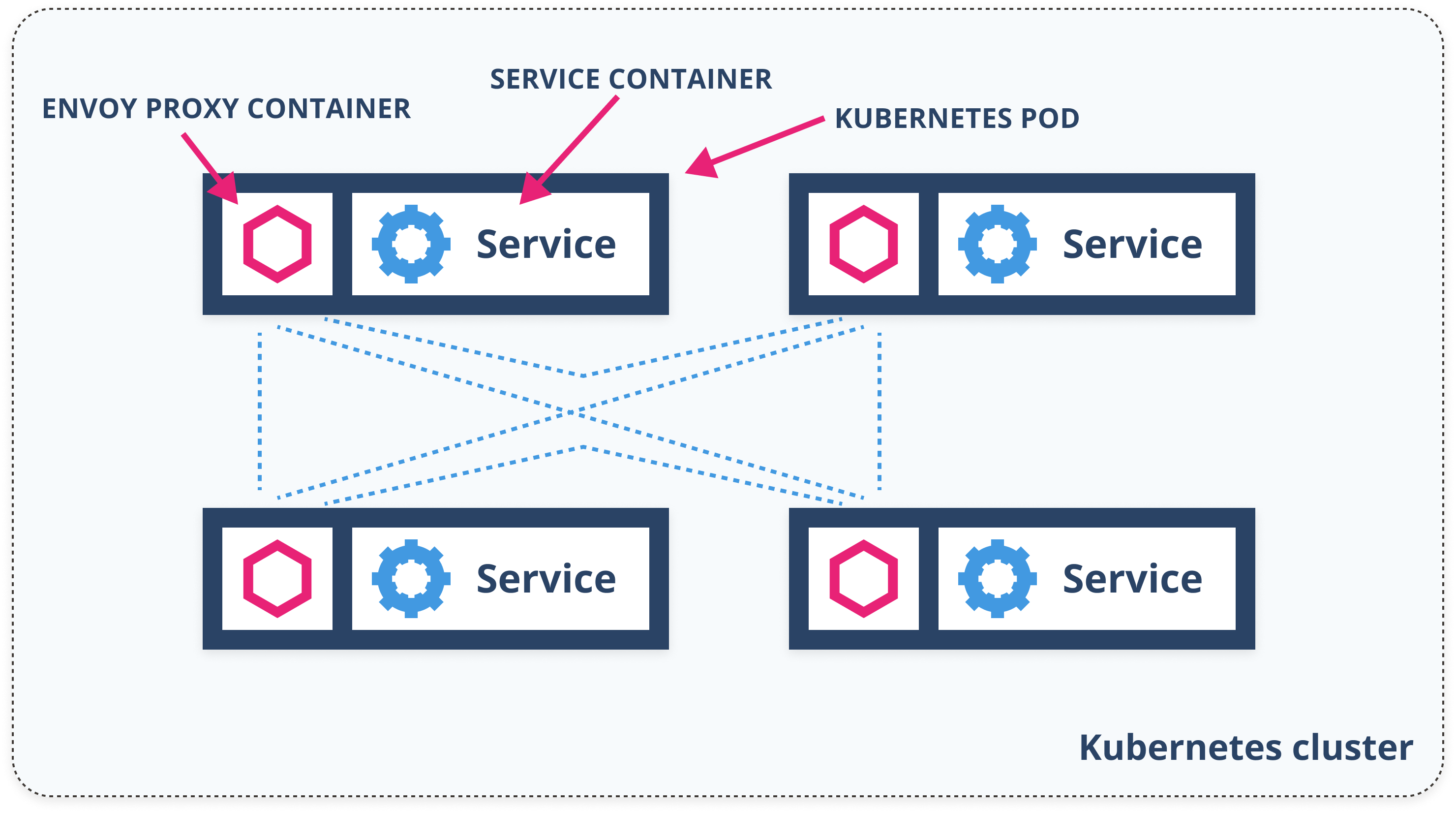
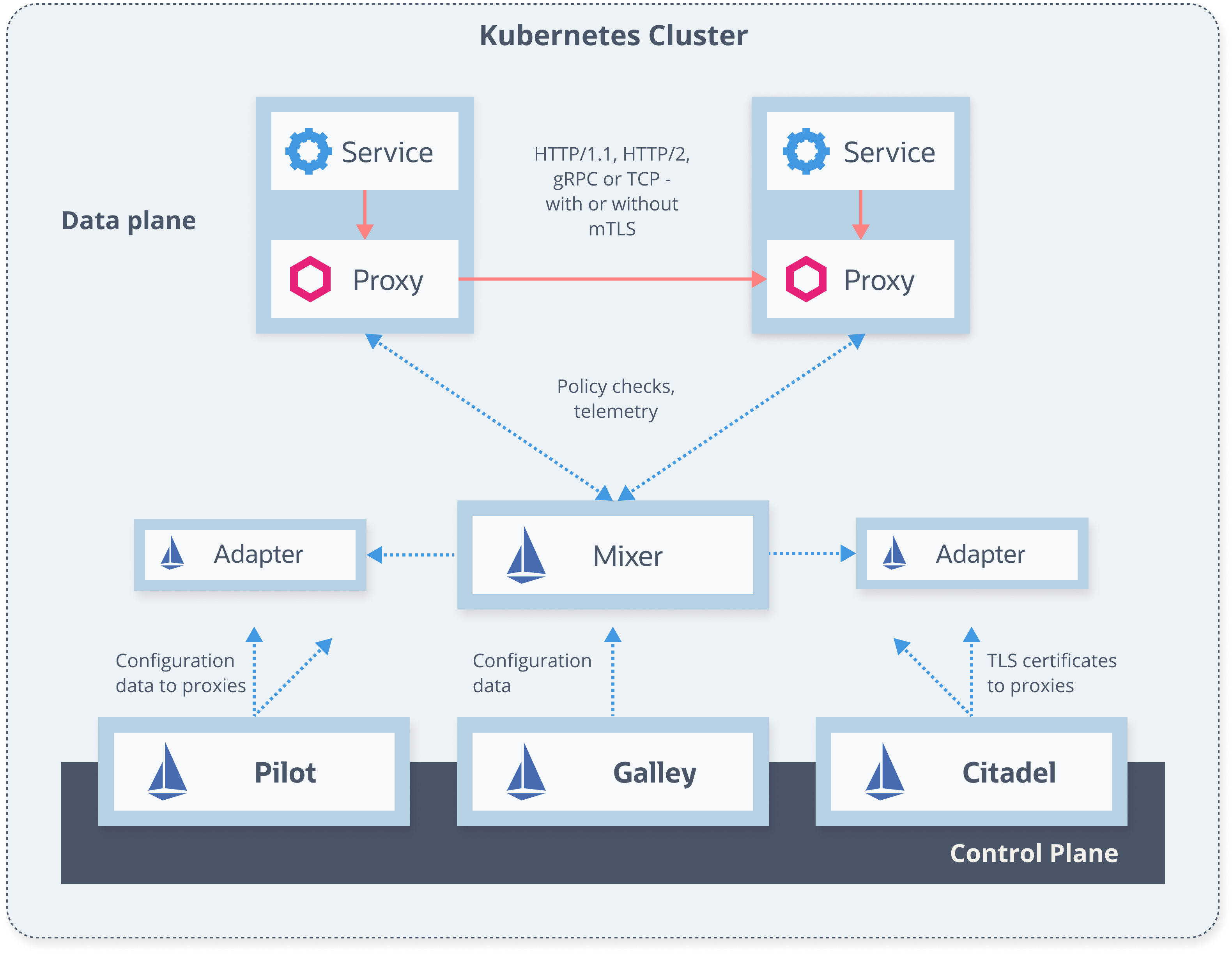
Service Mesh - Architecture
Data plane (proxies)
- Run next to each service instance (or one per host)
- Istio uses Envoy proxy
- Intercept all incoming/outgoing requests (
iptables) - Configure on how to handle traffic
- Emits metric
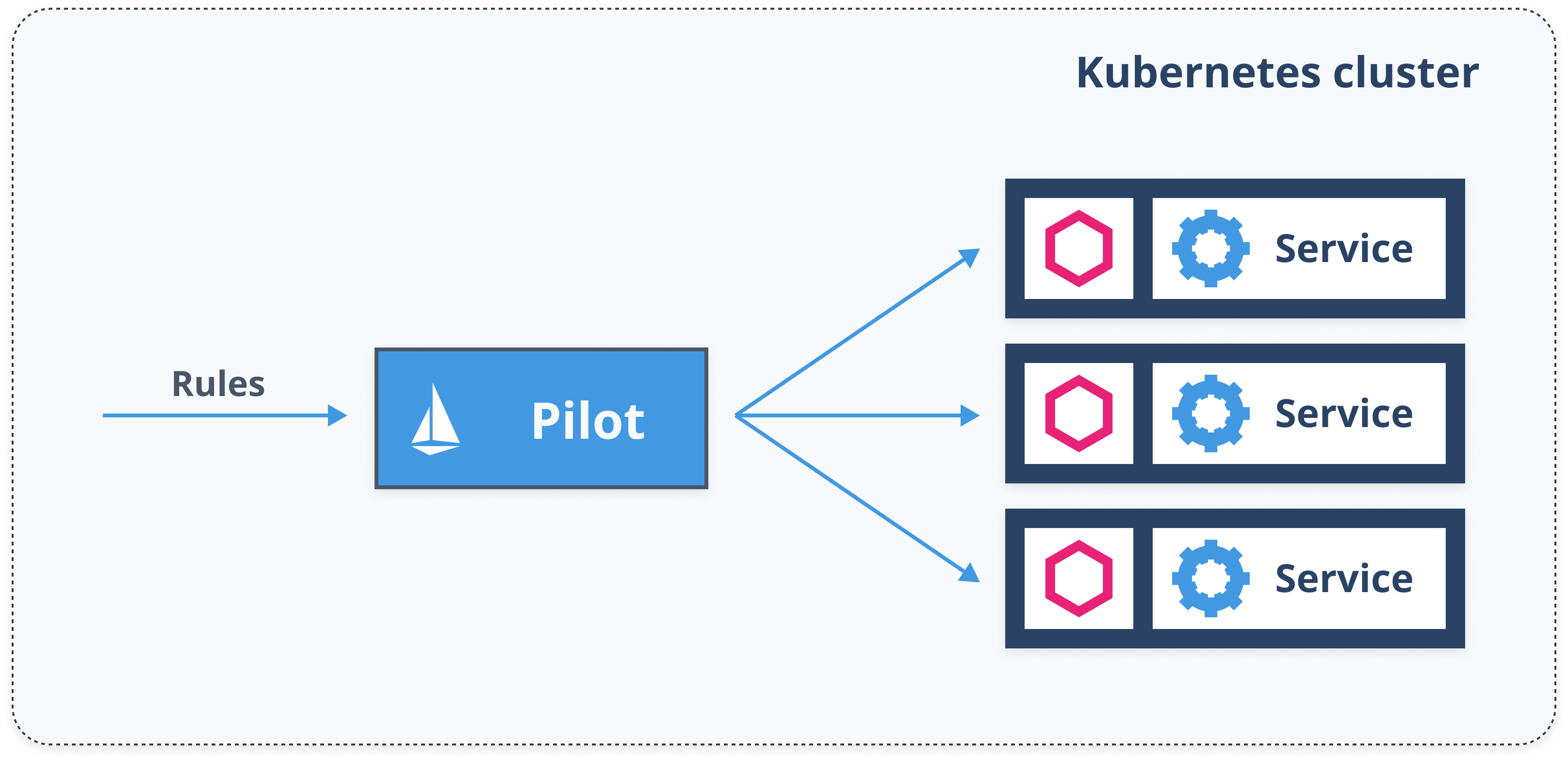
Control plane
- Validates rules
- Translates high-level rules to proxy configuration
- Updates the proxies/configuration
- Collects metrics from proxies
Service Mesh - Features
Connect
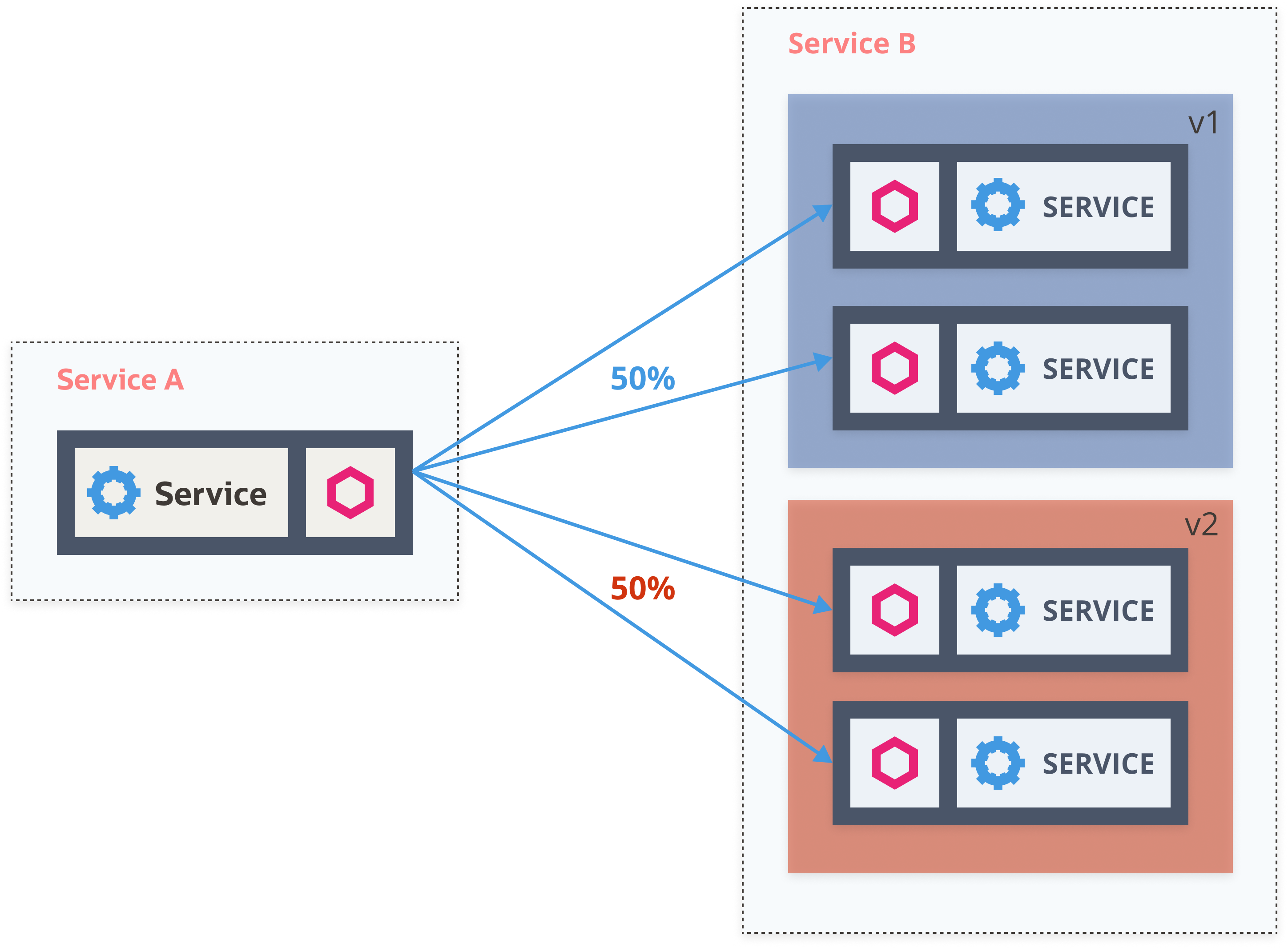
- Layer 7 routing and traffic management
- %-based traffic split (URIs, header, scheme, method, ...)
- Circuit breakers, timeouts and retries
Manage
- Telemetry (proxies collect metrics automatically -> tools: Grafana, Jaeger, Kiali)
- Visibility into service communication without code changes
Secure
- Secure communication between services (mutual TLS)
- Identity + cert for each service
Service Mesh - Istio
Traffic Management Resources
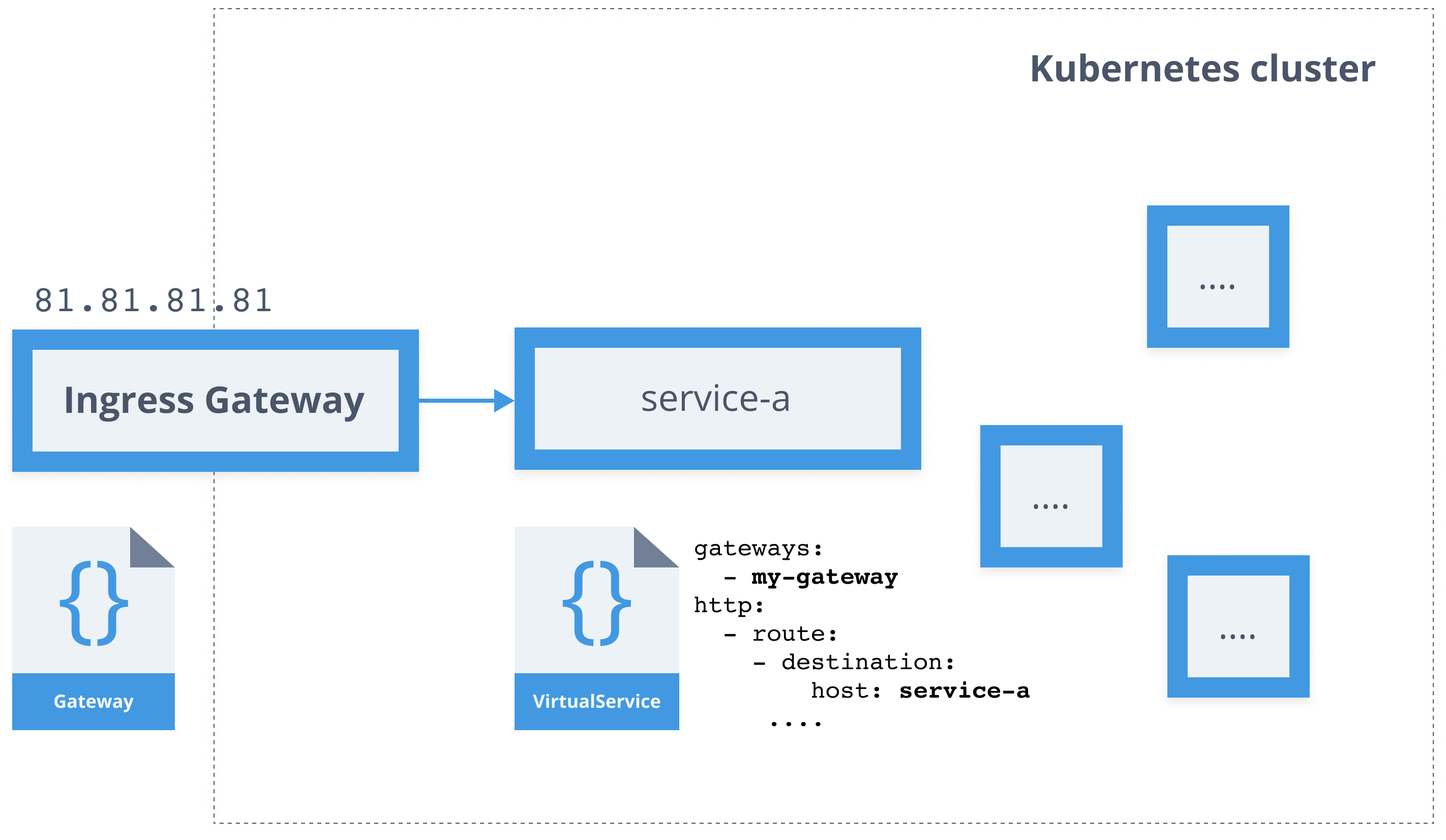
- Gateway
- VirtualService
- DestinationRule
- ServiceEntry
- Sidecar
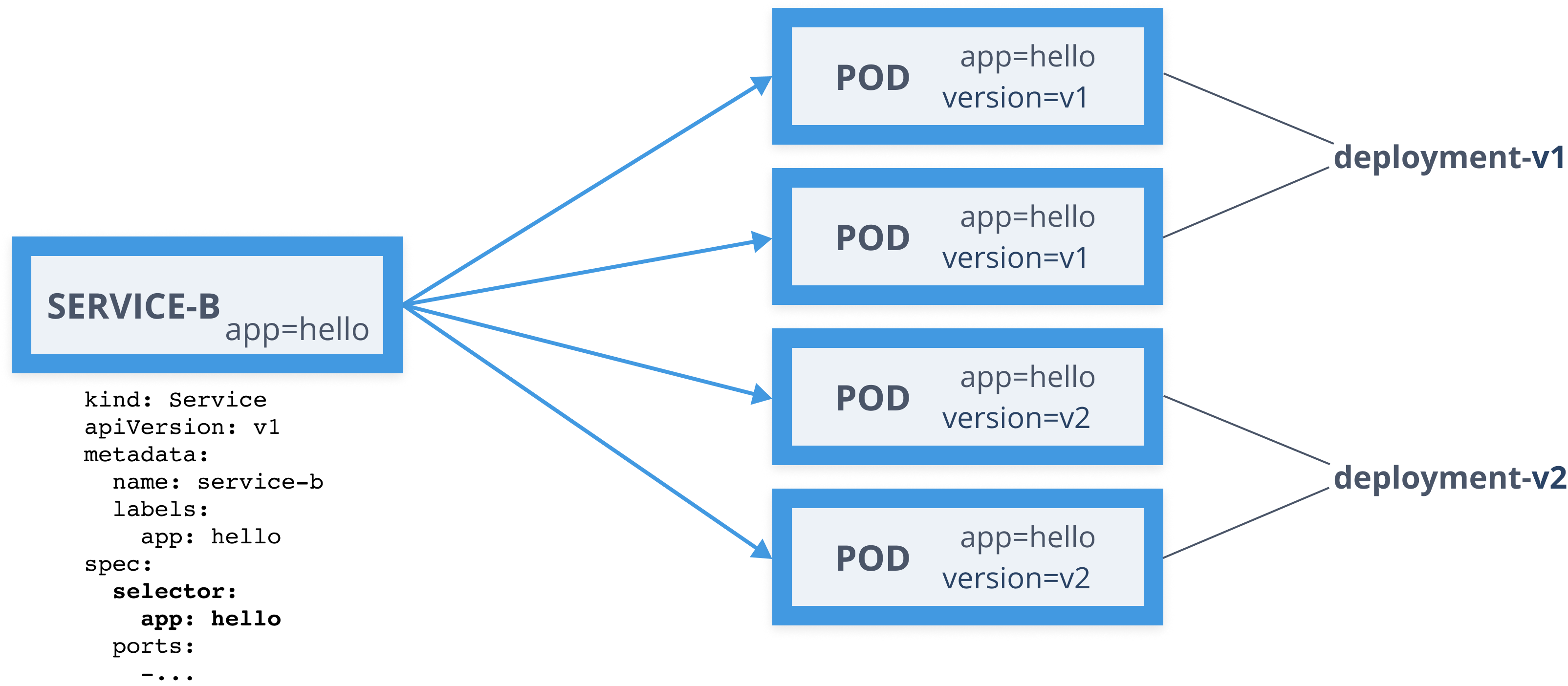
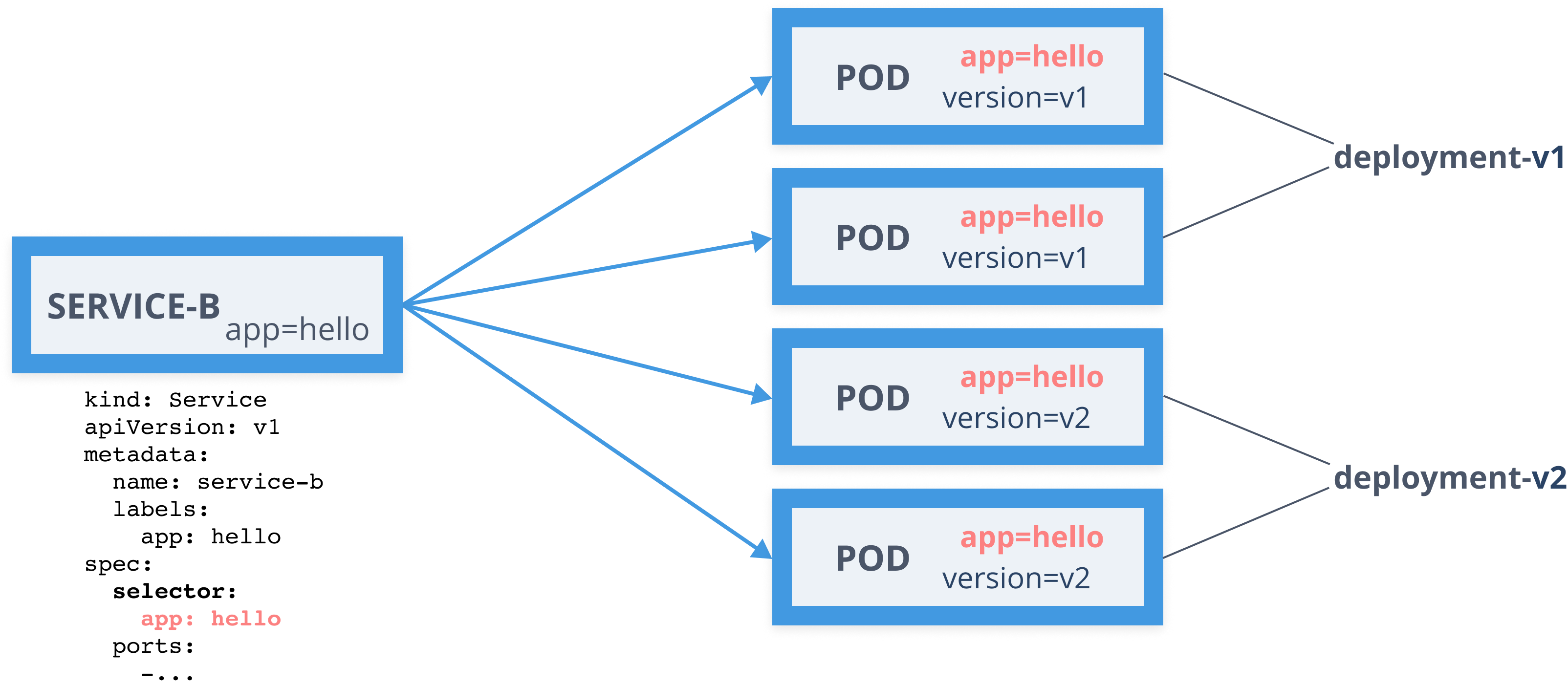
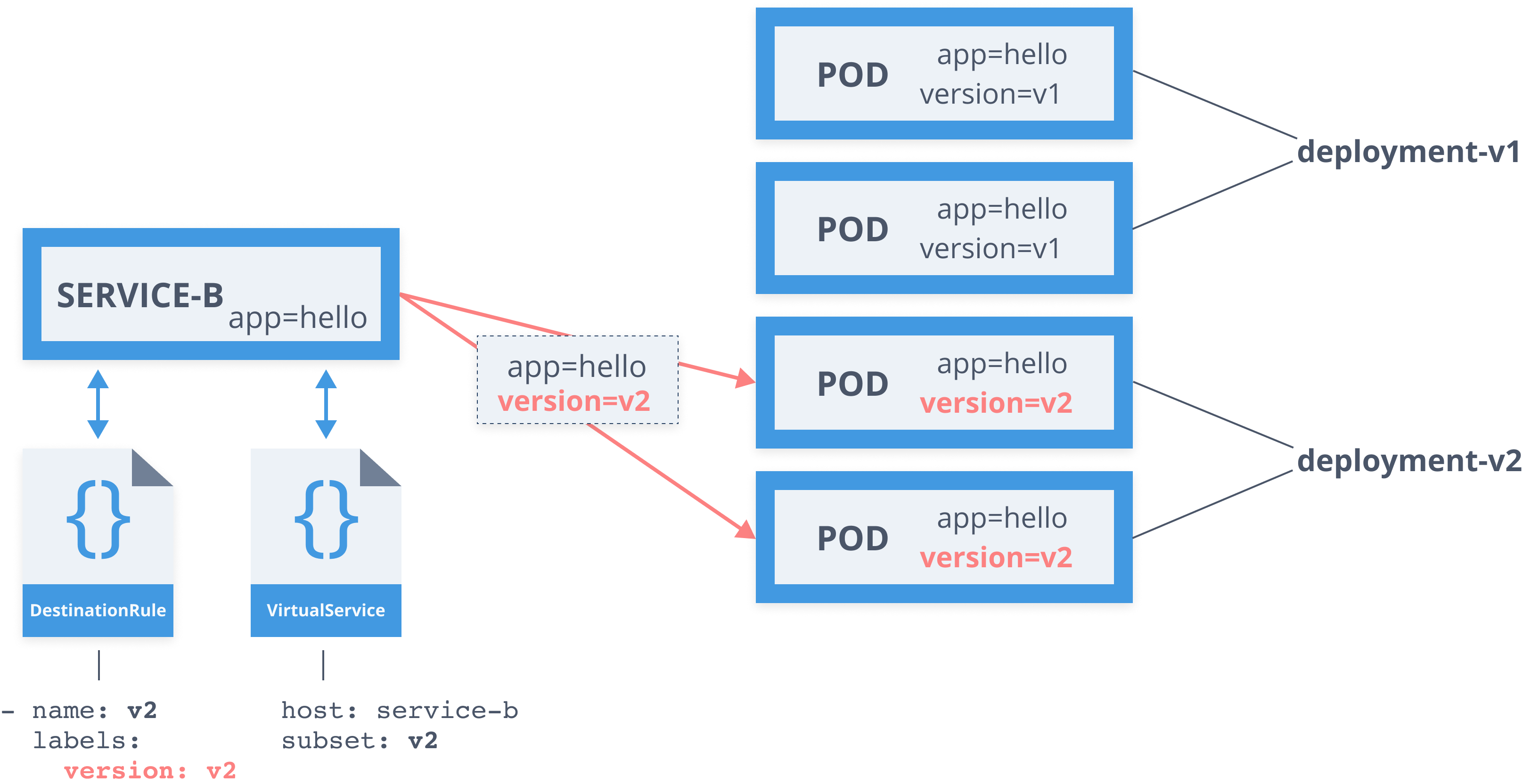
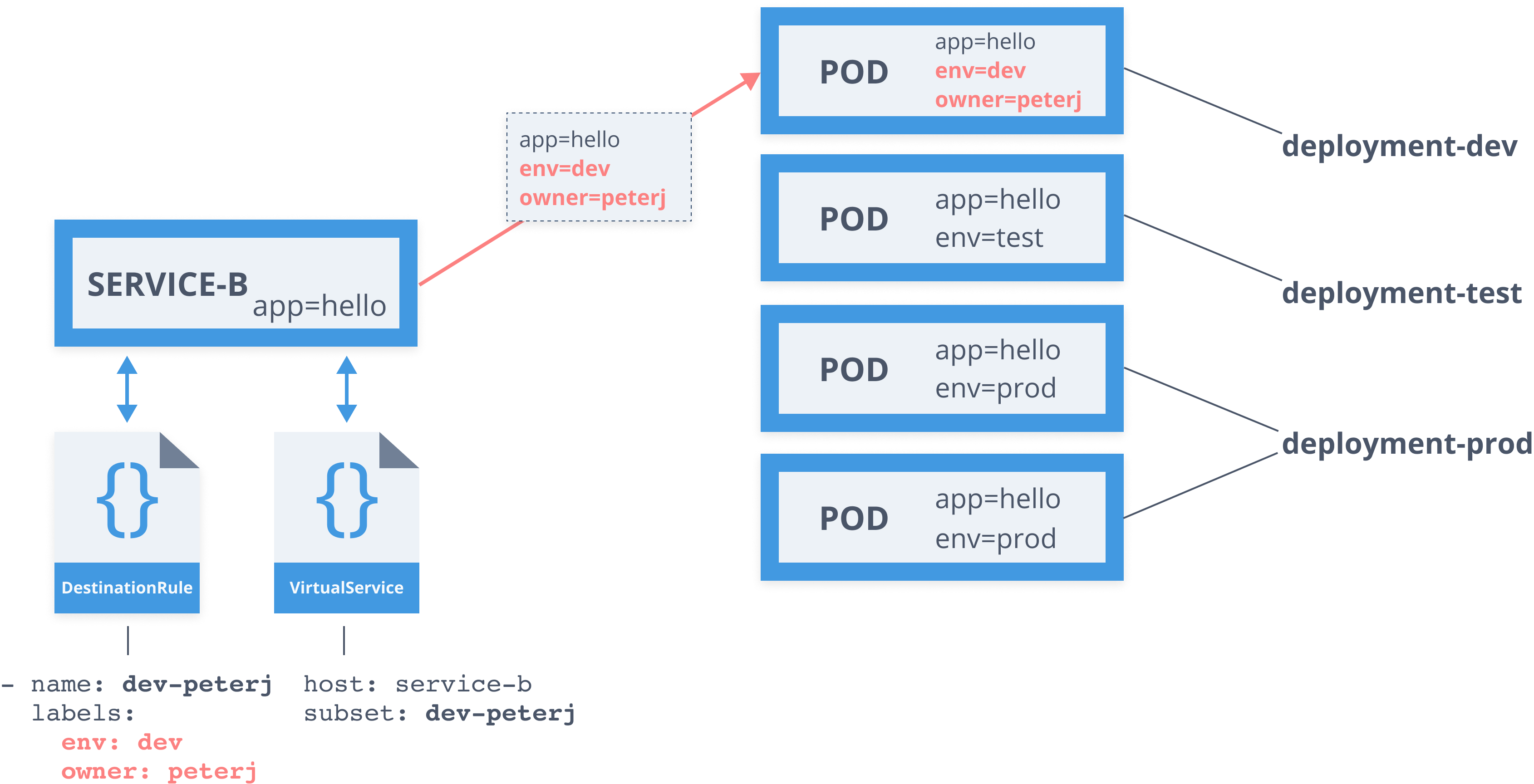
Service Mesh - Virtual Service
apiVersion: networking.istio.io/v1alpha3kind: VirtualServicemetadata: name: serviceb-vsspec: hosts: - service-b.default.svc.cluster.local http: - route: - destination: host: service-b.default.svc.cluster.local subset: v1 weight: 98 - destination: host: service-b.default.svc.cluster.local subset: v2 weight: 2Service Mesh - Destination Rule
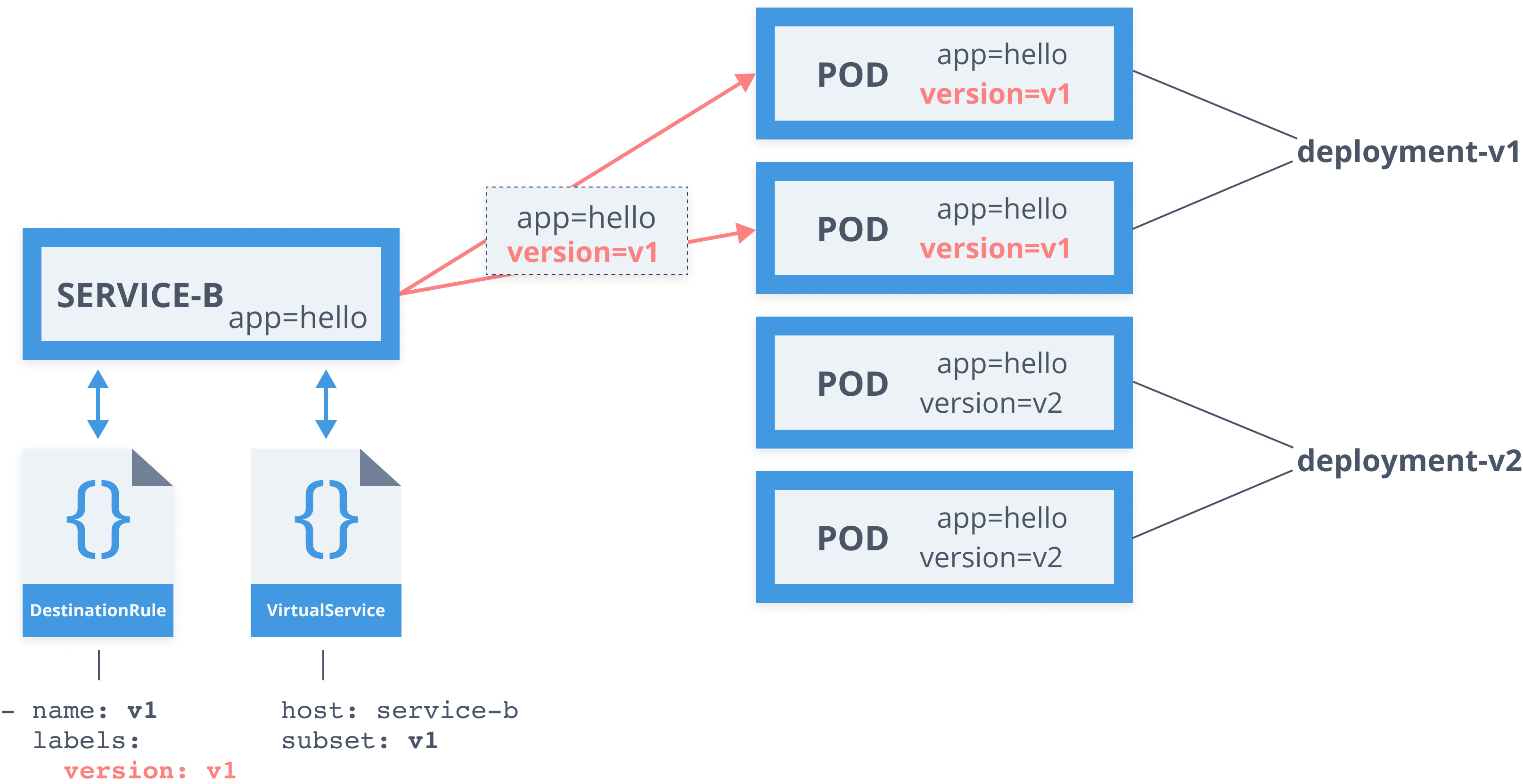
apiVersion: networking.istio.io/v1alpha3kind: DestinationRulemetadata: name: serviceb-drspec: host: service-b.default.svc.cluster.local subsets: - name: v1 labels: version: v1 - name: v2 labels: version: v2 trafficPolicy: tls: mode: ISTIO_MUTUALDestination rule
apiVersion: networking.istio.io/v1alpha3kind: DestinationRulemetadata: name: serviceb-drspec: host: service-b.default.svc.cluster.local subsets: - name: v1 labels: version: v1 - name: v2 labels: version: v2Virtual service
... http: - route: - destination: host: service-b.default.svc.cluster.local subset: v1 weight: 30Service Mesh - Service Entry
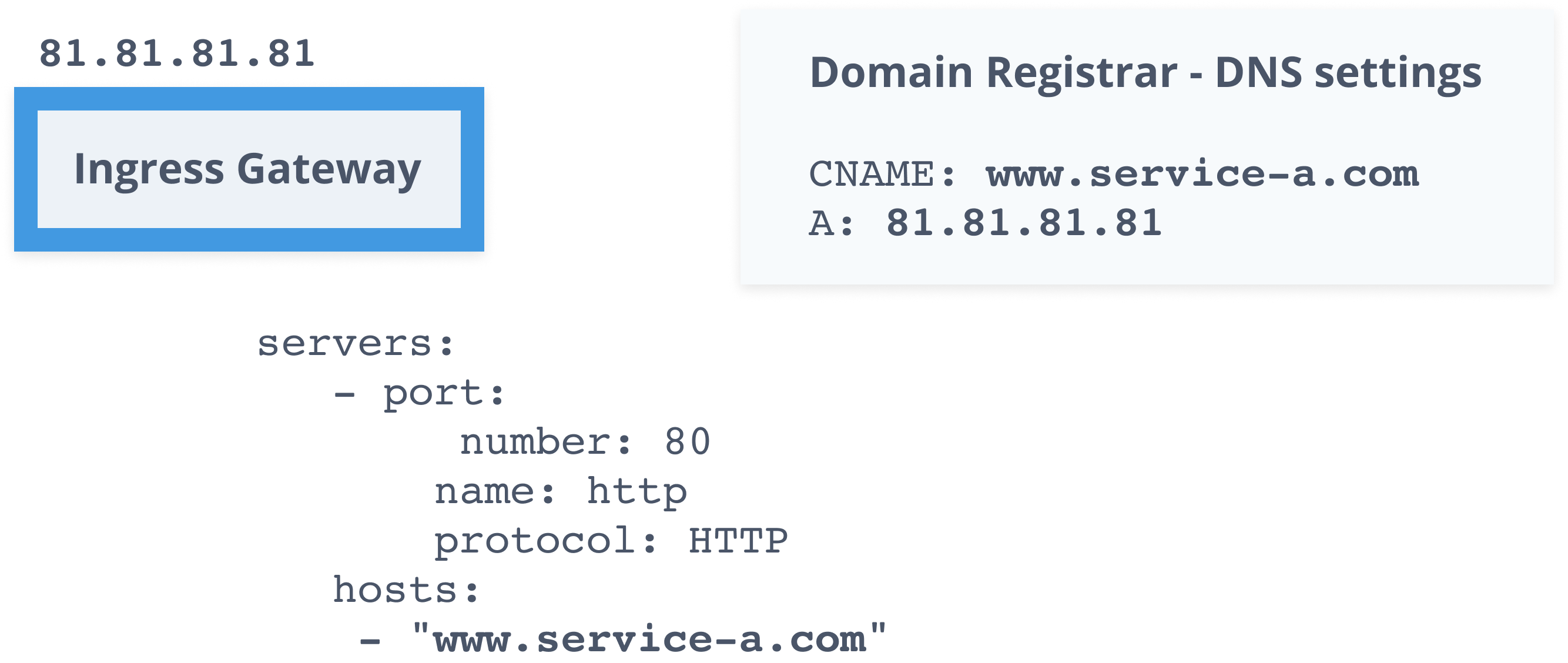
apiVersion: networking.istio.io/v1alpha3kind: ServiceEntrymetadata: name: movie-dbspec: hosts: - api.themoviedb.org ports: - number: 443 name: https protocol: HTTPS resolution: DNS location: MESH_EXTERNALService Mesh - Gateway
apiVersion: networking.istio.io/v1alpha3kind: Gatewaymetadata: name: gatewayspec: selector: istio: ingressgateway servers: - port: number: 80 name: http protocol: HTTP hosts: - "hello.example.com"Service Mesh - Sidecar
apiVersion: networking.istio.io/v1alpha3kind: Sidecarmetadata: name: default namespace: prod-us-west-1spec: egress: - hosts: - 'prod-us-west-1/*' - 'prod-apis/*' - 'istio-system/*'Service Mesh - Traffic Management
- Define subsets in DestinationRule
- Define route rules in VirtualService
- Define one or more destinations with weights
Resiliency
High availability
- Healthy
- No significant downtime
- Responsive
- Meeting SLAs
Disaster recovery
- Design can't handle the impact of failures
- Data backup & archiving
Resiliency Strategies
- Load Balancing
- Timeouts and retries
- Circuit breakers and bulkhead pattern
- Data replication
- Graceful degradation
- Rate limiting
Service Mesh - Timeouts
apiVersion: networking.istio.io/v1alpha3kind: VirtualServicemetadata: name: service-bspec: hosts: - service-b.default.svc.cluster.local http: - route: - destination: host: service-b.default.svc.cluster.local subset: v1 timeout: 5sService Mesh - Retries
apiVersion: networking.istio.io/v1alpha3kind: VirtualServicemetadata: name: service-bspec: hosts: - service-b.default.svc.cluster.local http: - route: - destination: host: service-b.default.svc.cluster.local subset: v1 retries: attempts: 3 perTryTimeout: 3s retryOn: gateway-error,connect-failureService Mesh - Circuit Breakers
apiVersion: networking.istio.io/v1alpha3kind: DestinationRulemetadata: name: service-bspec: host: service-b.default.svc.cluster.local trafficPolicy: tcp: maxConnections: 1 http: http1MaxPendingRequests: 1 maxRequestsPerConnection: 1 outlierDetection: consecutiveErrors: 1 interval: 1s baseEjectionTime: 3m maxEjectionPercent: 100Service Mesh - Delays
apiVersion: networking.istio.io/v1alpha3kind: VirtualServicemetadata: name: service-bspec: hosts: - service-b.default.svc.cluster.local http: - route: - destination: host: service-b subset: v1 fault: delay: percentage: 50 fixedDelay: 2sService Mesh - Aborts
apiVersion: networking.istio.io/v1alpha3kind: VirtualServicemetadata: name: service-bspec: hosts: - service-b.default.svc.cluster.local http: - route: - destination: host: service-b subset: v1 fault: abort: percentage: 30 httpStatus: 404Access Control
Can a principal perform an action on an object?
Principal = user
Action = delete
Object = file
Authentication (authn)
- Verify credential is valid/authentic
- Istio: X.509 certificates
- Identity encoded in certificate
Authorization (authz)
- Is principal allowed to perform an action on an object?
- Istio: RBAC policies
- Role-based access control
Identity - SPIFFE
- SPIFFE (Secure Production Identity Framework for Everyone)
- Specially formed X.509 certificate with an ID (e.g.
spiffe://cluster.local/ns/default/sa/default) - Kubernetes: service account is used
Mutual TLS (mTLS)
Flow
Traffic from client gets routed to the client side proxy
Client side proxy starts mTLS handshake
- Secure naming check: verify service account in the cert can run the target service
Client and server side proxies establish mTLS connection
Server side proxy forwards traffic to the server service
Configuring mTLS/JWT
- Policy resource (
authentication.istio.io/v1alpha1.Policy) Scope:
- Mesh < namespace < service
Also supports JWT
Configuring authorization
Who can talk to whom
- Uses RBAC (role-based access control)
Service role
- Actions that can be performed on service by any principal with the role
Service role binding
- Assigns roles to principals (principals = service identities = ServiceAccounts)
Configuring RBAC
- ClusterRbacConfig resource (
rbac.istio.io/v1alpha1) - Multiple modes:
- On, off
- On with inclusion, on with exclusion
How to get started?
- Do you need a service mesh?
- Start small and slow:
- Learn and understand the resources
- Apply to a subset of services
- Understand the metrics, logs, dashboards
Resources
- Kubernetes (OKE) on Oracle Cloud - https://cloud.oracle.com
- Kubernetes - https://kubernetes.io
- Istio - https://istio.io